Manage endpoints smarter with an automated solution for fast, effective vulnerability remediation.
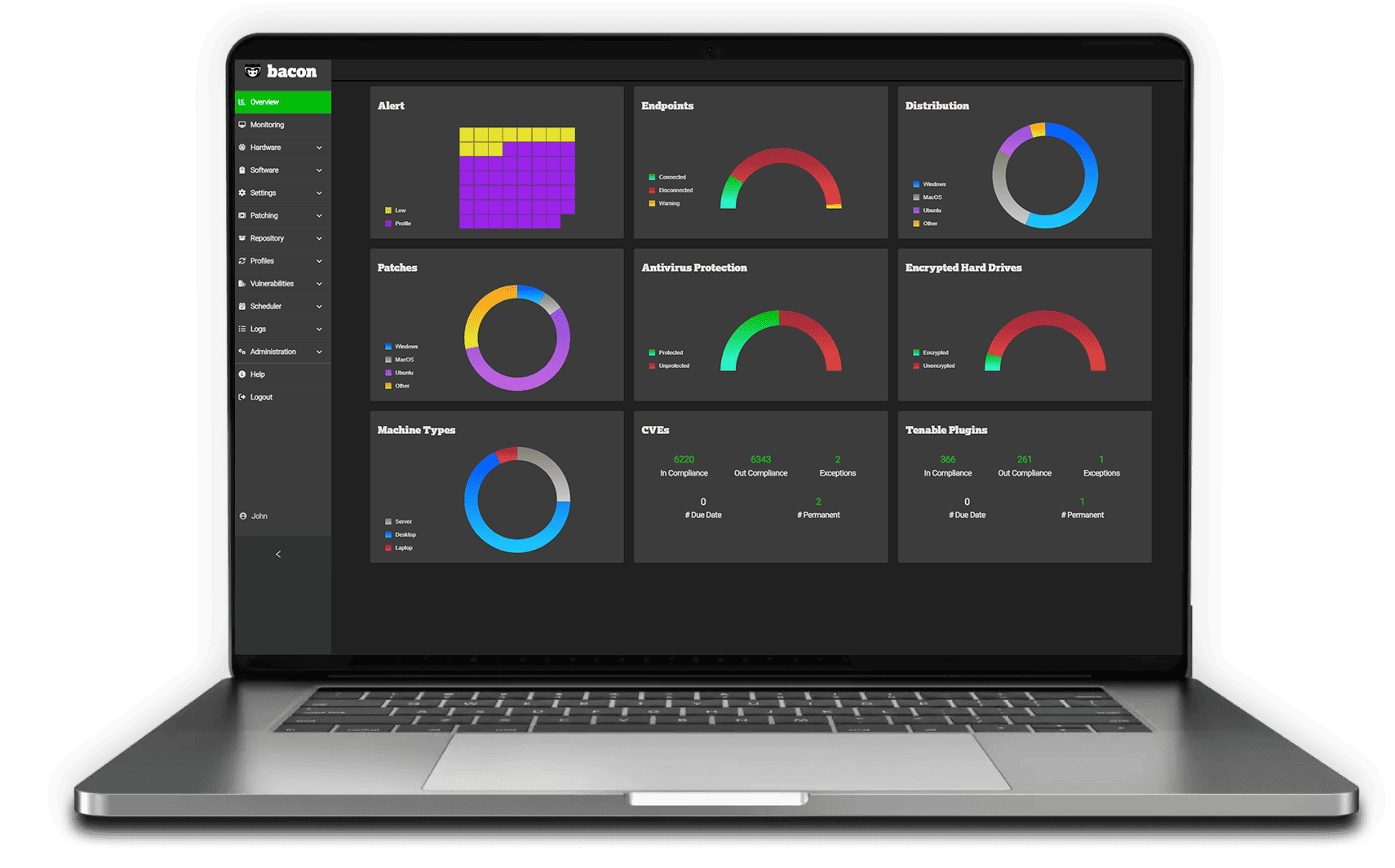
Bacon Unlimited® is unique in fixing vulnerabilities others miss—fast, flexible, and built for modern IT needs.
Fix vulnerabilities before they become threats instead of simply identifying them, by addressing outdated software, configurations, and third-party vulnerabilities.
Automate patching, software installs, and policy updates across thousands of endpoints to reduce IT workload and human error.
Manage Windows, macOS, and Linux devices from a single platform, ensuring all devices are secure and up-to-date.
Get immediate insights into the health and performance of all endpoints, so you can act on issues before they cause damage.
Designed for both speed and simplicity, Bacon’s interface allows IT teams to filter, search, and create dynamic groups with ease.

View Bacon Bits videos on application installation, system patching, endpoint configuration, scripting, and more. These Bacon Bits videos are all you need to get ready for your demo and installation.
Protecting your business isn’t just about fixing vulnerabilities—it’s about reducing risk, minimizing downtime, and maximizing efficiency. Bacon Unlimited turns security into a strategic advantage.
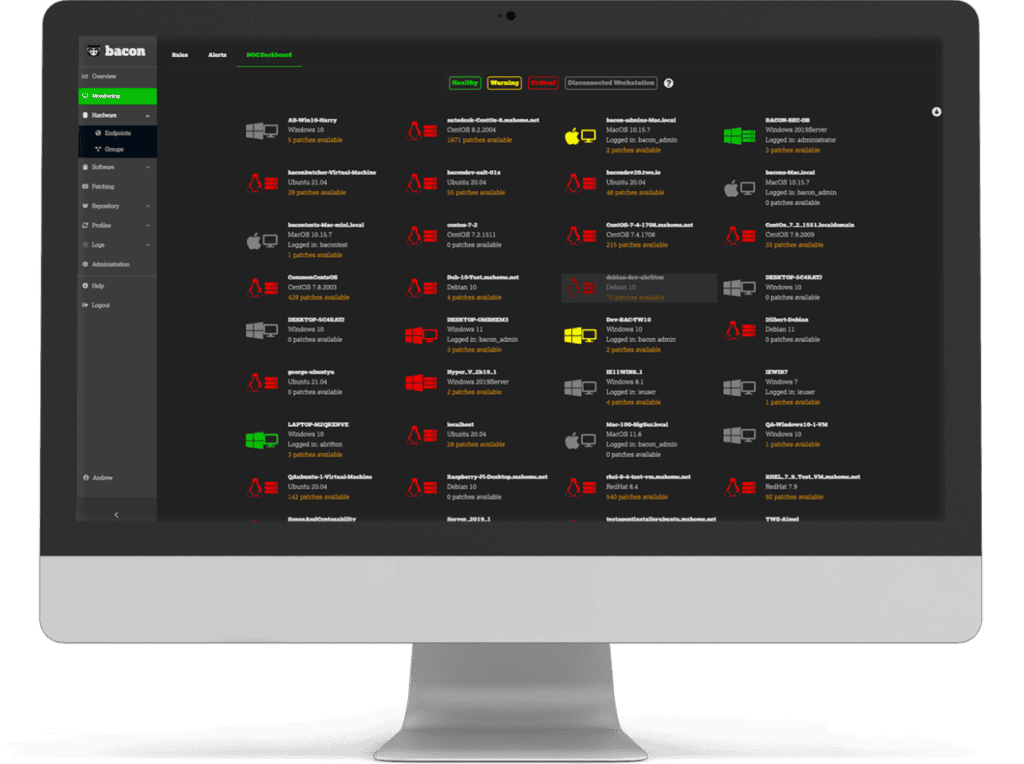

Reduce disruptions with near-instant fixes, keeping your business running smoothly.
Eliminate vulnerabilities quickly, protecting sensitive data and critical operations.
Automate compliance checks and reporting, saving time and avoiding fines.
Manage hundreds of endpoints without overloading your IT team or budget.
Free up IT teams to focus on strategic tasks, not manual patching.
From streamlined patching to instant vulnerability fixes, see how businesses like yours harness Bacon Unlimited to reduce risk, boost efficiency, and stay ahead of cyber threats—all in real time.





Sign up for Bacon’s exclusive mailing list, the Bacon Unlimited Flavor Force, to receive cutting-edge insights and updates straight to your inbox. Don’t miss out—become a Flavor Force member today and empower your IT operations with the best tools in the industry!
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |